The elasticity, scalability, and speed of the public cloud can help organizations reduce costs, manage data growth, and increase agility. For chief information officers (CIOs), however, moving to the hybrid or public cloud can present challenges. Red Hat’s hybrid cloud platform offers security, heterogeneity, and high performance that can span multiple cloud environments, allowing the deployment and management of applications […]
Read more ›
Seeping through the Gaps: Threats in Supply Chains and Development Pipelines
While DevOps has given organizations an option for a faster and more efficient development process, security is sometimes overlooked. With security breaches becoming more common, users must learn how leveraging security tools can help address issues before they arise and give you the visibility you need to overcome them. Read Seeping Through the Gaps to explore the threats we are […]
Read more ›
Untangling the Web of Cloud Security Threats
Cloud solutions are not something inherently good or bad for an organisation’s security. However, it requires organisations to understand the primary threats and challenges they face in a cloud environment and to change the way they think about cloud security: not as something that gets tacked on after the fact, but as an integral part of a well-designed cloud implementation. […]
Read more ›
Cloud Misconfigurations Cause Breaches – How to Avoid it
The common security challenges faced in the cloud stem from misconfiguration, compliance, and an exploding set of cloud infrastructure services. Hear about how to combat these challenges and gain visibility into security, compliance, and governance vulnerabilities on your public cloud infrastructure. Learn skills that will help you gain more free time and resources, while providing peace of mind that your […]
Read more ›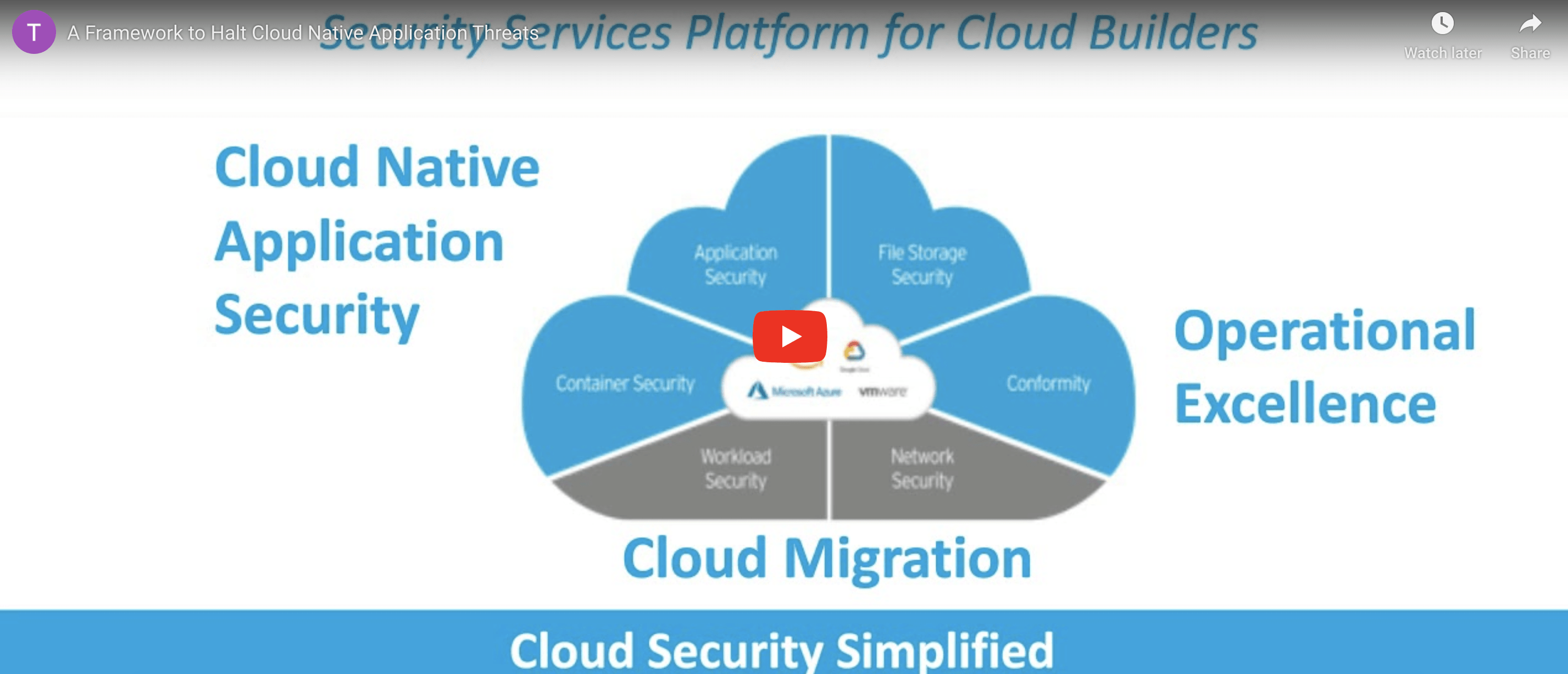
A Framework to Halt Cloud-Native Application Threats
Cloud-native applications continue to evolve at a rapid pace. With modern development practices and technologies, like CI/CD, containers, and serverless, your application security needs to provide early detection, immediate protection, and assurance that your cloud services meet security best practices. In this recording, you’ll learn about:• Security concerns of cloud-native application development and deployment• Security automation and best practices for […]
Read more ›
Undertaking Challenges in Hybrid Cloud Security Environments
How can you secure your apps and services without compromising your schedule? (Hint: It’s all in the automation.) Enterprises are using hybrid cloud technologies to enrich the user experience and power their digital transformation. But running applications in public clouds while managing the application data in private clouds makes for a unique set of security requirements. We discuss the challenges […]
Read more ›
Finding the Best WAN Edge Solution for Your Enterprise: Criteria for Evaluating SD-WAN (Buying Guide)
When a network is working well, enterprises enjoy improved application performance, lower costs, and stronger business continuity. When a network isn’t working well, enterprises feel the pain. The truth is, not all network solutions are created equal. When considering a new SD-WAN solution, there are important differences you need to understand to ensure that you’re identifying the right factors critical […]
Read more ›
Citrix SD-WAN on AWS Use Cases
Don’t let legacy WAN technologies handicap your cloud migration. Download a short technical white paper from Citrix that explains how Citrix SD-WAN delivers enhanced connectivity between AWS and distributed branch offices by: • Providing excellent quality of service (QoS) with intelligent traffic management and WAN optimization• Ensuring high-quality connections through dynamic path selection and sub-second failover• Allowing organizations to consolidate […]
Read more ›


