On-Demand Webcast: Privileged Account Governance Delivers 360-Degree View
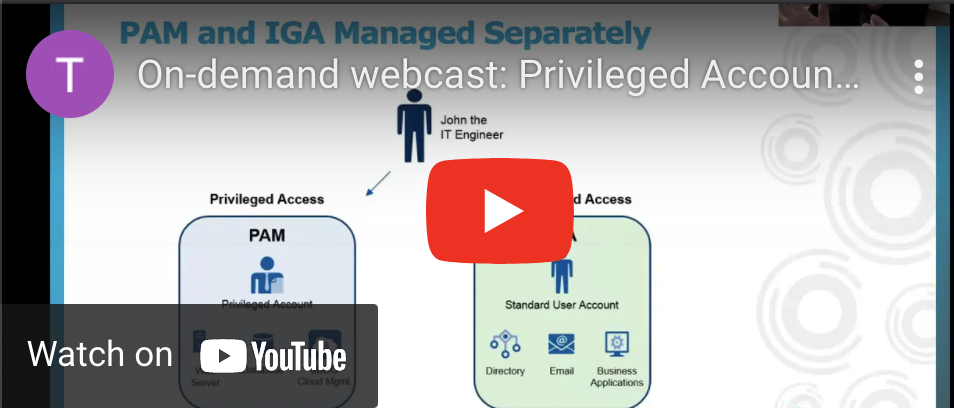
The term ‘privileged access’ is a hot topic lately. It refers to connecting to and managing your critical accounts, which enable your organization to run smoothly. Protecting these accounts should be the first priority when it comes to cybersecurity.
With everything you and your team have going on – including making your digital transformation – and the constant threat of a breach, how do you protect and efficiently manage these accounts, and control who has access to them? By integrating your identity governance and administration (IGA) and your privileged access management (PAM) systems to achieve privileged access governance (PAG).
Organizations that operate their PAM and IGA technologies as integrated systems can more easily perform a number of critical security-related functions. They can:
• Apply identity-provisioning process to privilege accounts
• Enforce cohesive access policies across target systems and platforms
• Take advantage of modern governance capabilities
• Get a 360-degree view of users, accounts and activities
View this on-demand session: Learn how One Identity’s Privileged Account Governance (PAG) module bridges the security and management gap between IGA and PAM.

