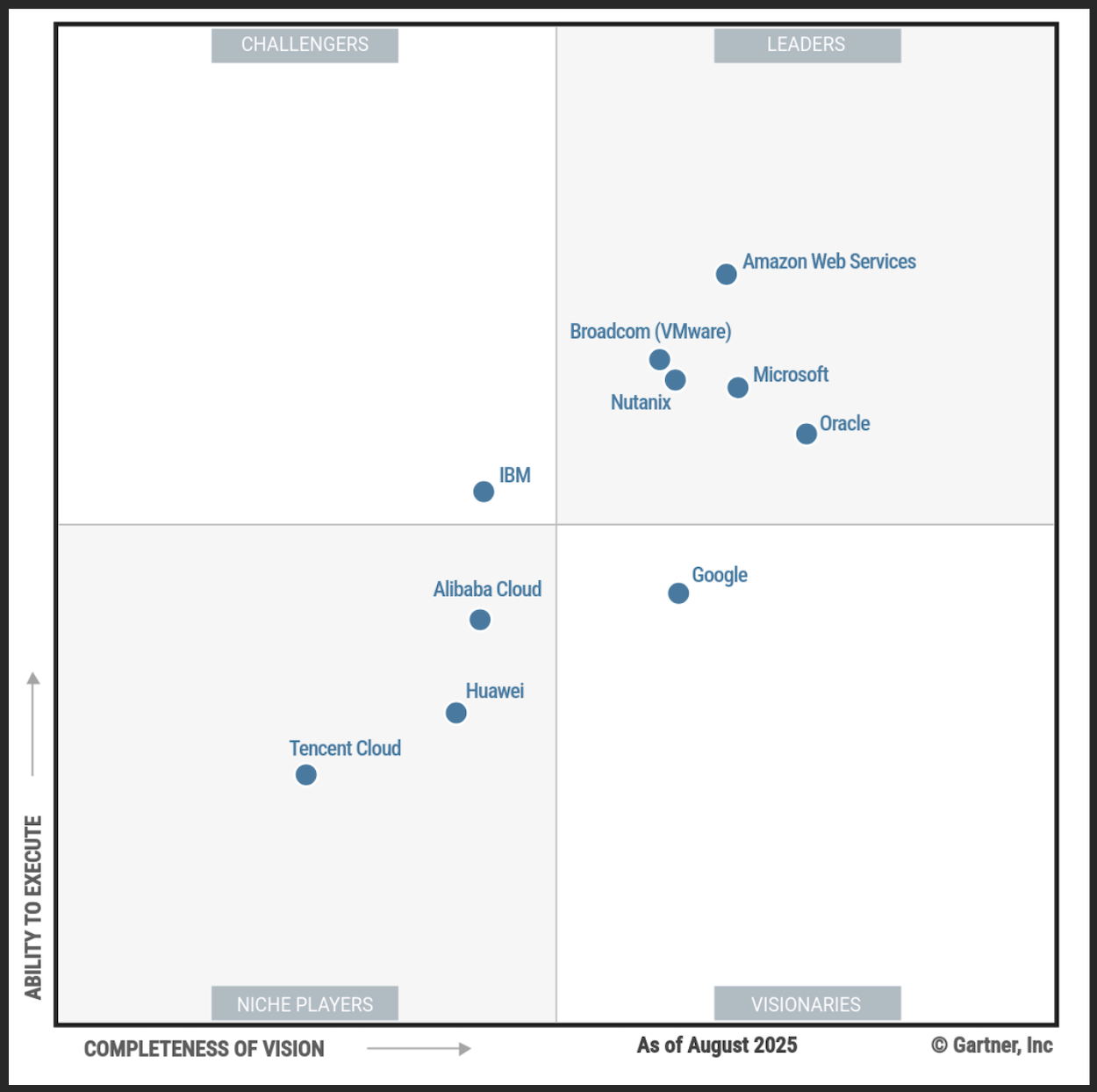
Understanding VMware Alternatives
Broadcom’s acquisition of VMware has triggered widespread confusion, frustration, dissatisfaction, and reports of high costs across the IT landscape. In a new research brief from NAND, discover how forward-thinking IT leaders are turning disruption into opportunity. Learn how moving beyond VMware can unlock modern alternatives that drive efficiency, agility, and performance, while enabling next-gen capabilities […]
Read →