Articles By: RSA
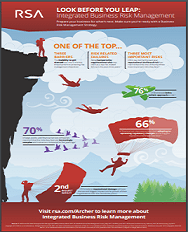
Look Before You Leap: Integrated Business Risk Management
By understanding information security risk, compliance risk, and business risk within a single framework, business leaders can make better decisions and ensure that the organization’s objectives are met. View the infographic to discover the facts of integrated business risk management and to learn why taking a holistic approach to risk should be a top priority in your organization.

How GRC Can Help You Stay a Step Ahead of Ransomware
With ransomware growing at 350% annually,* many federal, state and local governments, and private-sector businesses, are focused on the question of how to better prepare for the next attack.

The 10+1 Guiding Principles of Business Risk Management
Your business risk management program should add strategic value to the organization—enabling the business to focus on strategic objectives and optimize performance, not just simply meet compliance requirements. Ultimately, business risk management is about making decisions— decisions to manage, accept, transfer or avoid risk.

Forrester Wave Security Analytics
Security Analytics Platforms, Q1 2017. In their 36-criteria evaluation of security analytics (SA) providers, Forrester identified the 11 most significant ones and researched, analyzed, and scored them. Download this report to see why RSA was named a Leader and how SA solutions enable security and risk professionals to detect, investigate and respond to cybersecurity threats.

Business-Driven Security and the GDPR. GDPR Data Protection and RSA NetWitness® Suite – White Paper
The EU’s General Data Protection Regulation (GDPR) will affect any company that does business within the EU and goes into effect on May 25, 2018. The GDPR represents a major evolution in global data security and privacy practices, so companies will need to thoroughly review, and in many cases drastically change, the way personal data is handled going forward.

Kingslayer – A Supply Chain Attack
RSA Research investigated the source of suspsicious, observed beaconing thought to be associated with targeted malware. In the course of this tactical hunt for unidentified code, RSA discovered a sophisticated attack on a software supply-chain involving a Trojan inserted in otherwise legitimate software; software that is used typically used by enterprise system administrators.

The 7 Building Blocks of Better Threat Visibility – eBook
IF YOU CAN’T SEE IT, YOU CAN’T STOP IT. So how do you detect something, like a zero-day threat or a new strain of malware, that no one has ever seen before?

The 3 Keys to Faster Threat Response – eBook
90 percent of security professionals polled say they’re unsatisfied with how quickly they are able to react to threats. They need deeper insights into user behavior and other variables, an instant understanding of the full scope of threats, and more context to set priorities. What can you do to speed things up?


