Articles By: HPE

Let UX drive DevOps eBook
Focusing on the user experience will improve your apps, your business results, and your success with DevOps. This report discusses the implication of UX on DevOps and explains what needs to be measured and monitored to do DevOps successfully. Find out how you can keep up with user expectations and build and release quality software faster and more frequently.

Cyber Risk Report 2016: Executive Summary
Hacker attacks are evolving to target applications and to focus on financial gain. Attacks on Linux, Android, and OS X continue to grow. And government regulations threated to drive legitimate security research underground. Those are some of the findings of this year’s deep dive into the cyber threat landscape by HPE Security Research.
Information Governance Considerations in the Life Sciences Industry
Translating compliance and information governance concepts into actionable strategies can be challenging for life sciences organizations. But it is definitely a priority. Facing the challenge involves following a phased approach encompassing communication, a degree of “cultural evolution,” and of course, leveraging good technology.
Information Governance Considerations and Big Data In The Financial Services Sector
Learn how you can manage Big Data in the financial services sector and protect yourself from an uncertain future.

Forrester Report: Six Trends That Will Shape DevOps Adoption in 2015 and Beyond
Infrastructure and operations (I&O) organizations are in various stages of adopting the DevOps methodology. Where does your organization fall in comparison with other organizations? This Forrester Whitepaper presents strategic benchmarks that I&O professionals can use to see where they are in their DevOps adoption compared with their peers.

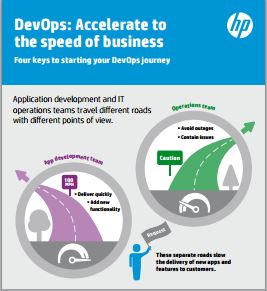
Four Keys to your DevOps Journey
This eBook elaborates on the challenges business have in their high-velocity organizations, detailing how to use the four key steps to make “DevOps” a reality.

The ESG Cybersecurity Maturity Model
How does your cyber security program compare to other companies? Where do your security people, processes, and technology place you among peer organizations? And more important, what should be your next steps to improve your program? Based on their research, Enterprise Strategy Group has developed a cyber security maturity model that classifies organizations as basic, progressing, or advanced.