
Driving Strategic Value with IBM Sterling Supply Chain Business Network
Modern business-to-business (B2B) integration is critical to increasing revenue, speeding up time to market and improving efficiencies. That is why many enterprises have opted for cloud B2B integration and have chosen IBM Supply Chain Business Network.
Deepen B2B Transaction Visibility
Are you struggling to get the information you need from your supply chain? See how business transaction intelligence featuring Watson can help you analyze data up to 90% faster and reduce time to value by up to 85%.

Cloud Enabled Threats Guide
New insights into threats, trends and tactics The cyber kill chain has migrated to the cloud. Do you understand the new security threats well enough to take the right protective measures? Read the report that exposes the latest cloud-enabled threats and explains why they elude traditional defenses.

Use Case-Driven Web Security Evaluator Guide
85% of today’s web gateway traffic is related to apps and cloud services, according to new research. What’s the implication for web security, and what tactics can you employ to thwart new attacks? Read the eBook that describes the top 7 use cases for Secure Web Gateway (SWG) solutions in the cloud era.

Hilton Enhances Digital Guest Experience With Red Hat Container And Automation Technology
As the hospitality industry expands and evolves, leading global hospitality company Hilton is focused on continuing to enhance its innovative guest services and amenities with digital offerings. The company decided to build an agile hybrid cloud computing environment to speed application development and deployment with continuous integration and continuous delivery (CI/CD) and automation capabilities.
Debunking the Myths of Hybrid Cloud Adoption
IT departments are better prepared to support changing business requirements with flexible hybrid cloud provisioning and management platforms. Microsoft and Red Hat enterprise customers have a proven foundation to support the development of their own open source strategy. Download this analyst paper to learn how.
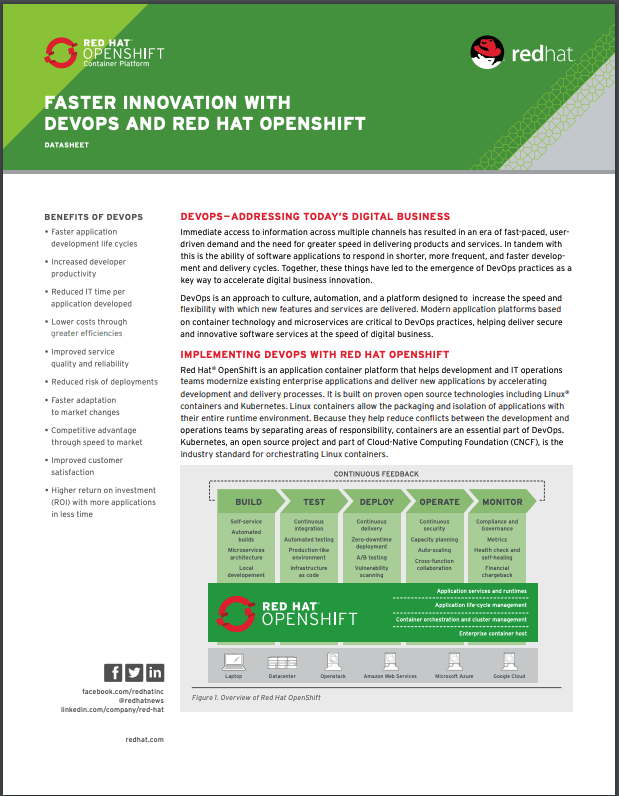
Accelerate your DevOps with OpenShift
In this datasheet, you’ll learn how Red Hat® OpenShift®—an application container platform—helps development and IT operations teams embrace DevOps to better modernize existing apps and deliver new ones with an accelerated delivery process.

The Business Value of an Agile and Flexible Platform for Developing and Running Applications With OpenShift on AWS
IDC spoke with organizations that are using containers in the public cloud with Red Hat OpenShift and Amazon Web Services (AWS) to develop and run business applications. These organizations reported benefiting from combining a powerful and flexible container platform with the agility, elasticity, and efficiency of the AWS cloud.


