
Solution Brief: Flash-Optimized Storage and Integrated Availability for the Always-On Enterprise
The exponential growth of data and provisioned IT services is forcing businesses and enterprises of all sizes to rethink their Availability strategy.

Solution Brief: Protect Your Data From Malicious Ransomware Threats
This data availability best practice is designed to ensure that all businesses effectively prepare for and avoid potential data loss and downtime from ransomware attacks. By following industry best practices, IT managers can avoid paying ransom and create a rock-solid data availability solution for day-today operations by leveraging both HPE and Veeam® software.

Application Management: Racing Ahead of the Competition
Application complexity, emerging architectures and siloed IT infrastructures bring new challenges—and opportunities—to application management. Just as IT needs a management tool that addresses overall service availability and performance, application managers need a platform that transcends the silos—incorporating and analyzing data from the various sources that influence performance and availability.

Path to Operational Intelligence
Turning big data noise into valuable IT and business information follows a predictable pattern—what Splunk calls the path to Operational Intelligence. With Splunk as your platform for Operational Intelligence, moving from reactive problem solving to real time, data driven insights is not only within reach, it’s easier than you think.
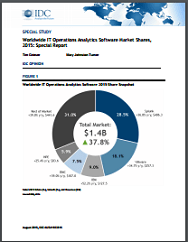
Worldwide IT Operations Analytics Software Market Shares
IDC, a leading provider of global IT research and advice, has published its estimate of market sizes and vendor market shares for the rapidly growing ITOA software market. In the report, learn who shaped the year for ITOA, market share, market context and significant market developments for ITOA and principal benefits of ITOA for IT organizations.

Security Investigation, Detection & Rapid Response With Splunk Enterprise
Hunting for an unknown threat or investigating an alert or breach can prove challenging and time-consuming for anyone—whether that’s a dedicated analyst or a person that plays multiple roles. the security analytics cycle.

Machine Data eBook (Security)
Organizations must use every available resource to protect against the latest cyberattacks, the persistent nature of advanced threats, and the ease with which malware can cripple an entire network. One of the most important—and often overlooked—resources that organizations can tap into is machine data.

Six Essential Capabilities of an Analytics-Driven SIEM
SIEM (security information and event management) software offers a lot of promise, but legacy SIEMs simply can’t keep up with the rate and sophistication of today’s cyberattacks. Learn how to dramatically improve your security posture, advanced threat detection and incident response.


