Articles By: Trend Micro

Top Three Benefits of Migrating to SAAS
You have enough to worry about. Don’t add an on-premises solution to that list. Read this paper to learn about the many benefits of migrating to the cloud.

Cloud Migration: Achieve More Together With Four Security Considerations
We’re not playing the “What if?” game anymore when it comes to cloud. The conversation has shifted to when and how you can get cloud done, and in turn, how can you make sure all of your cloud workloads are truly secure?

Seeping through the Gaps: Threats in Supply Chains and Development Pipelines
While DevOps has given organizations an option for a faster and more efficient development process, security is sometimes overlooked. With security breaches becoming more common, users must learn how leveraging security tools can help address issues before they arise and give you the visibility you need to overcome them.

Untangling the Web of Cloud Security Threats
Cloud solutions are not something inherently good or bad for an organisation’s security. not as something that gets tacked on after the fact, but as an integral part of a well-designed cloud implementation.
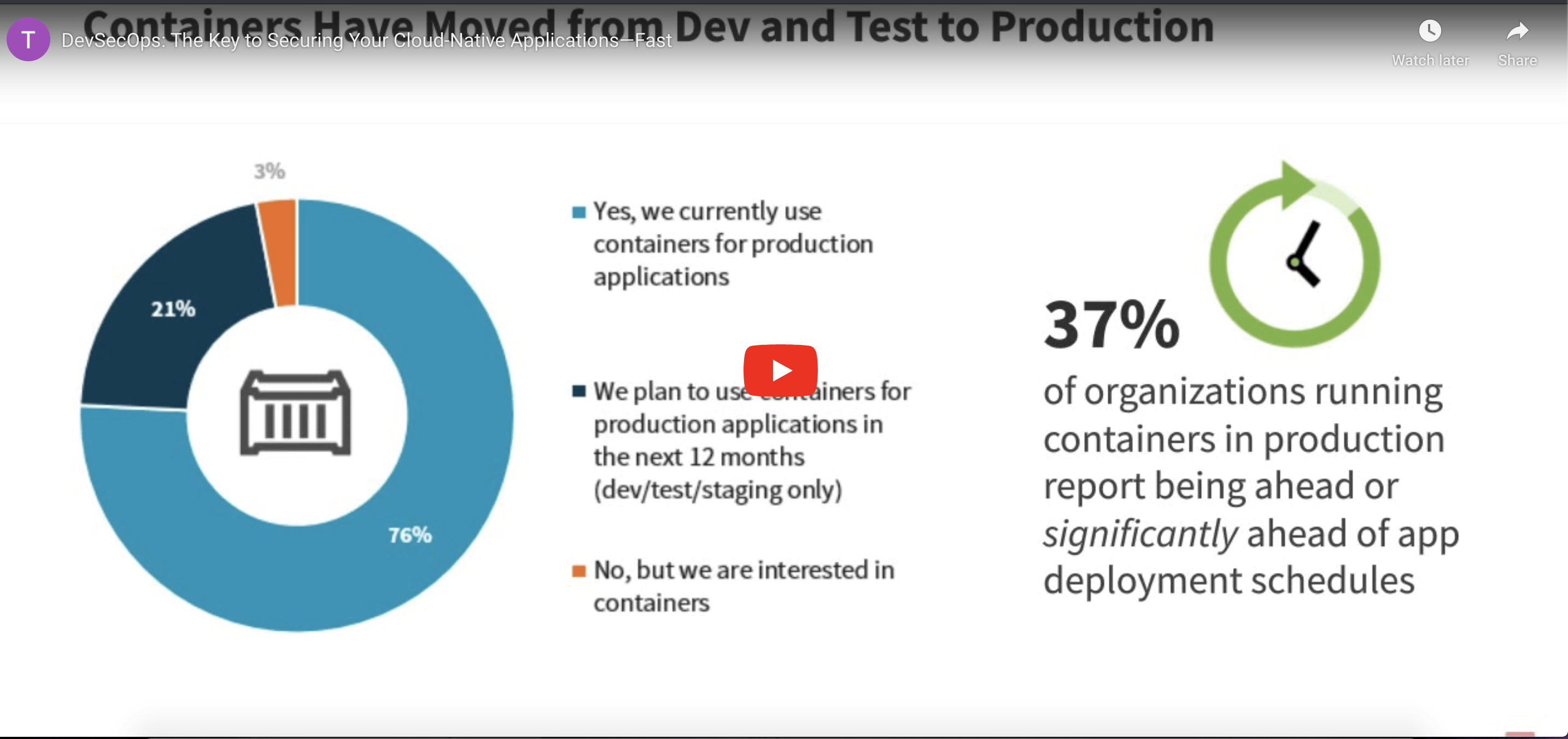
DevSecOps: The Key to Securing Your Cloud-Native Applications—Fast
As you transition your workloads to container, Kubernetes®, and serverless environments, a unified development and deployment approach requires increased involvement of the cybersecurity team. Listen as Doug Cahill, Senior Analyst and Group Director, ESG and David Clement, Product Marketing Manager Hybrid Cloud, Trend Micro, discuss how DevSecOps is being used to artfully secure cloud-native applications.

Principles to Make Your Cloud Journey More Secure
If you have just started your cloud migration journey, you’re in the right place! Join our webinar to gain the tools to smooth out your transition to the cloud. Hear from Trend Micro’s Principal Engineer and Cloud Advisor, Jason Dablow, about the art of migrating applications to the cloud—utilizing the scalability and agility of these hyper-dynamic environments.

Mind the Gap: Building a Closer Relationship Between Security and DevOps
Unleash the Benefits of Unifying Security and DevOps Reducing the gap between security and DevOps can unify your organization and allow for greater productivity.

Cloud Misconfigurations Cause Breaches – How to Avoid it
The common security challenges faced in the cloud stem from misconfiguration, compliance, and an exploding set of cloud infrastructure services. Hear about how to combat these challenges and gain visibility into security, compliance, and governance vulnerabilities on your public cloud infrastructure.


