Articles By: Trend Micro
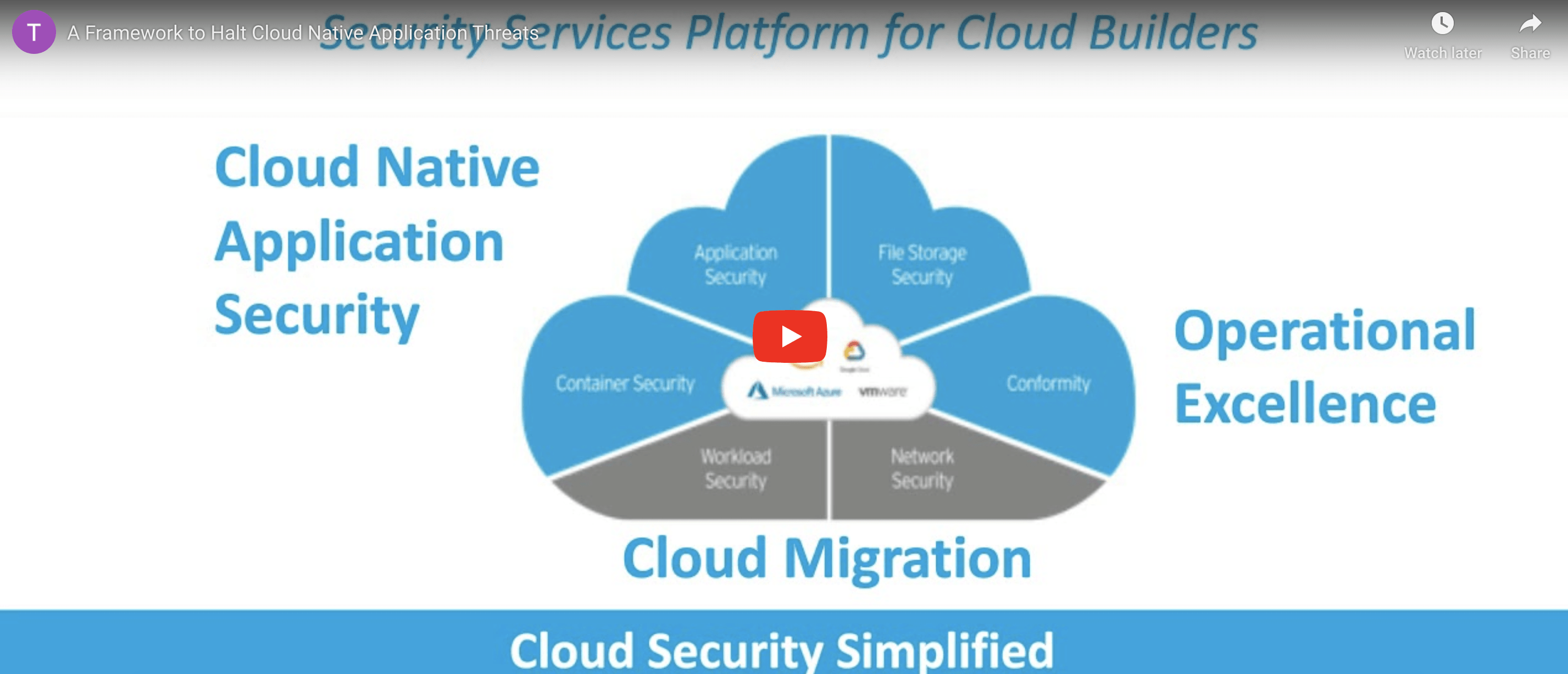
A Framework to Halt Cloud-Native Application Threats
Cloud-native applications continue to evolve at a rapid pace. With modern development practices and technologies, like CI/CD, containers, and serverless, your application security needs to provide early detection, immediate protection, and assurance that your cloud services meet security best practices.

Undertaking Challenges in Hybrid Cloud Security Environments
How can you secure your apps and services without compromising your schedule? ( It’s all in the automation.) Enterprises are using hybrid cloud technologies to enrich the user experience and power their digital transformation. But running applications in public clouds while managing the application data in private clouds makes for a unique set of security requirements.

The Secure DevOps Imperative: Three Best Practices for Securing Cloud-Native Applications
Enterprises are shifting to a cloud first application development strategy. As organizations transition to workloads, containers, Kubernetes, and serverless environments, a unified development and deployment approach requires increased involvement of the cybersecurity team.

Security by Design—Full Life Cycle Container Security that Matches the Speed of DevOps
In this webinar we outline the key steps and tools that will help you artfully automate full life cycle container security, including useful APIs, image scanning and runtime protection to detect problems early and mitigate against attacks targeting your host, Docker®, and Kubernetes® platforms and containers.
Security by Design—Kubernetes or Docker Deployments with Fast, Automated Protection
Join Trend Micro’s Principal Engineer and Cloud Advisor, Jason Dablow, as he takes you through art of building better applications that meet the speed and demands of your business—driving a successful DevOps practice.

AppSec Trend Report
To meet new market opportunities, as well as competitive and regulatory requirements, the software development life cycle has gone through several changes. DevOps methodologies are being adopted to develop and deploy applications at a faster, more sustainable rate.

Automated Security at the Speed of DevOps
DevOps has broken down silos between development and operations teams to help businesses shorten development life cycles and meet increased business demands. However, many are still struggling to incorporate security teams into their DevOps practices. These businesses need a solution that protects applications stacks and complies with the AWS Shared Responsibility Model, without limiting development speed.

Using Trend Micro’s Hybrid Cloud Security Solution to Meet PCI DSS 3.2 Compliance
Compliance continues to be a growing concern for organizations, especially for those leveraging virtualization and cloud computing. This paper examines Trend Micro™ Deep Security™ and its ability to secure Payment Card Industry (PCI) data in accordance with the PCI Data Security Standard (PCI DSS) 3.2 when used in physical, virtual, cloud, or container environments.


