
Incident Response Guide
What’s the best way to stop a cyberattack from turning into a full breach? Prepare in advance. Often, after an organization experiences a breach, they’ll realize they could have avoided a lot of cost, pain, and disruption if they had an incident response plan in place.

3M HEALTH INFORMATION SYSTEMS: Scaling Cloud Knowledge to Scale Cloud Operations
Scaling cloud knowledge across a quickly growing team — and across distributed geographies — is no easy feat. See how 3M Health Information Systems is using A Cloud Guru to create training “waves” to build skills quickly across the organization.

Capital One Leading in Cloud By Investing in People
Capital One is a leader in cloud adoption Capital One was one of the first enterprises to understand the potential of the public cloud, recognizing the unmistakable value in the agility, productivity, security, and efficiency that building on it provides. To help achieve their cloud-based transformation, Capital One developed Tech College to serve as its internal tech-learning organization.

The GCP Dictionary of Pain
We analyzed millions of responses to hundreds of our hardest questions based on the performance of our learners in those questions. From that, we analyzed some of the top terms and concepts that can trip us up—and help us all get on the same page when we know what they are.

State of Cloud Q3 2022
Disconnect Between Cloud Technologists and Business LeadersFindings of this report reveal a disconnect between organizational and individual cloud maturity. Business leaders reported high confidence in their organizations’ cloud strategies while individual contributors report feeling new to cloud technologies.

Technology Skills Development: Preparing Your Teams for Digital Transformation
Our Technology Skills Development (TSD) Workbook walks you through TSD best practices with questions to help you create a custom strategy that fuels growth, produces measurable return on investment (ROI) and boosts employee engagement and retention. These courses align to the workbook and dive deeper to help take your TSD strategy to the next level.
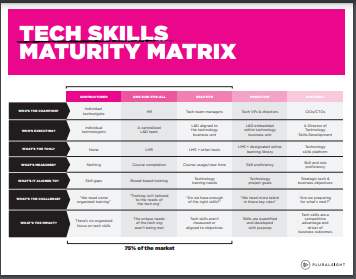
Tech Skills Maturity Matrix
CIOs are tasked with more today than ever before, including their organization’s speed, growth, innovation and efficiency. In order to have the capabilities on their teams to execute on these opportunities, skill development needs to be a strategic priority. For most organizations, this isn’t true today.

State of UpskillingReport 2022
Upskilling is a pivotal tool in your organization’s success roadmap. That’s no longer up for debate. However, what that upskilling looks like can vary, and your approach can transform your results.We surveyed 750+ technologists across all industries to get a clear picture of the state of upskilling in tech today.


